Overview
Recent decades, IC 61850 compliant substation automation systems SASs are being developed with more advanced features, including remote control, easy auto-configuration, and high-speed real-time communication. However, with the introduction of portals allowing external access, these new features also increase potential cyber security vulnerabilities. In addition, the end-point devices, such as intelligent electronic devices and remote terminal units, usually come from different vendors and cannot be fully trusted. From the design specification stage to the deployment and operational stage, a new device may become an untrusted component at any point.
Untrusted devices may stealthily perform harmful or unauthorised behaviours which could compromise or damage secondary plant systems, and therefore, bring severe impacts to the primary plant and even the entire electrical grid. Therefore, the overall objective of this project is to develop a method for identifying anomaly behaviours of untrusted control devices in SASs, especially for detecting false data injection attacks and messages modification attacks.
Outcomes
Software-based simulation tested, generated datasets, and an effective method to detect anomalies with high accuracy.
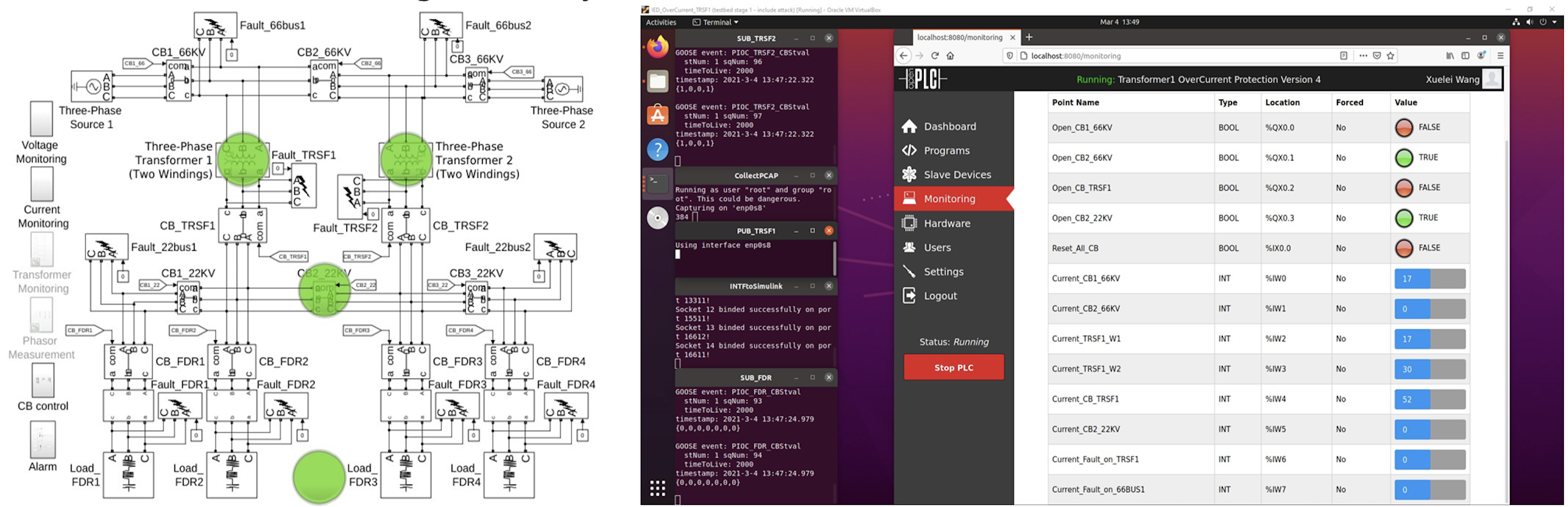
Key features and advantages
- The tested is cost-efficient and extendable. It simulates a IC 61850 compliant SASs which is close to real systems.
- The feature selection and extraction methods during data pre-processing are applicable to identify anomalies for both fault situation and attack scenarios.
- The proposed method improve the accuracy of detecting such insider attack scenarios by decreasing the false-negative rate from 50% to 5%.
- The proposed method researches the key hyper-parameters (window size and step size) when applying sliding window algorithms. The suggested window size and step size ensure the detection time is less than 3ms while also keep a high detection accuracy with 99%.
For further detail: Wang, X., Fidge, C., Nourbakhsh, G., Foo, E., Jadidi, Z., & Li, C. (2021). Feature selection for precise anomaly detection in substation automation systems. Paper presented at the Proc. 13th IEEE PES Asia Pacific Power and Energy Engineering Conference, Kerala, India.
Funding
Amount:
Duration:
Partners:
- Cyber Security Cooperative Research Centre